
In most SoC and FPGA designs, hardware security is now as important as power, area, and cost. In fact, the National Institute of Standards and Technology (NIST) reported a record number of Common Vulnerabilities and Exposures (CVEs) in 2021, and the year is not over yet. Given the difficulty of patching hardware, architecture choices along with an established security focused verification methodology must be in place to circumvent weakness in the logic that, if exploited, results in a negative impact to the chip’s security triad (confidentiality, integrity, or availability).
To help remediate security risk in hardware devices, in Feb. 2020, the MITRE Corporation released version 4.0 of their (CWE) list. The new version, for the first time, provides a valuable list of common hardware weaknesses, in addition to its software weaknesses, that are the root causes of many vulnerabilities.
The hardware list is categorized into major themes such as Security Flow Issues, Debug and Test Problems, Memory and Storage Issues, General Circuit and Logic Design Concerns, and so on. The CWE list has been developed to help design teams as they quantify risk exposure. In addition, it provides a valuable guide for threat modeling and secure design. By identifying potential issues early, the projected cost of a security incident can be significantly lowered or eliminated.
Over the last year, the list has continued to expand and as of version 4.6 (Oct. 28, 2021), it contains 98 common hardware weaknesses. While many of these vulnerabilities can be avoided with good architectural choices, others can be avoided with a mature design verification methodology that takes advantage of RTL static analysis.
Take for example, CWE-1245: Improper Finite State Machines (FSMs) in Hardware Logic. This CWE highlights that FSMs, if not constructed correctly, can allow an attacker to put a system in an undefined state, to cause a denial of service (DoS) or gain privileges on the victim’s system.
Many secure data operations and data transfers rely on the state reported by a FSM. Faulty FSM designs that do not account for all states, either through undefined states (left as don’t cares) or through incorrect implementation, might lead an attacker to drive the system into an unstable state from which the system cannot recover without a reset, thus causing a DoS. Depending on what the FSM is used for, an attacker might also gain additional privileges to launch further attacks and compromise the security guarantees.
With simulation alone, it is difficult to verify a complex FSM as it requires complex test vectors with both positive and negative testing to check all combinations of possible states. Fortunately, a mature RTL static verification tool such as Blue Pearl Software’s Visual Verification Suite provides without any need for test vectors, finite state machine analysis that automatically extracts the FSM from surrounding code, then checks for dead or unreachable states as well as generating an easy-to-read bubble diagram to better visualize the FSM and its potential vulnerabilities.
In addition, the suite also provides checks for coding style conformance, structure, race conditions (CWE-1298), resets (CWE-1271), as well as specific checks for functional safety protocols such as DO-254 conformance.
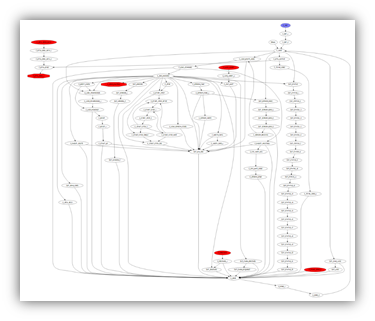
Complex Finite State Machine
Design teams that leverage static verification as part of their functional verification methodology are proven to reduce hardware security risks, as well as expensive and time-consuming simulation, synthesis and place and route runs and reruns, freeing up expensive licenses as well as improving overall design productivity.
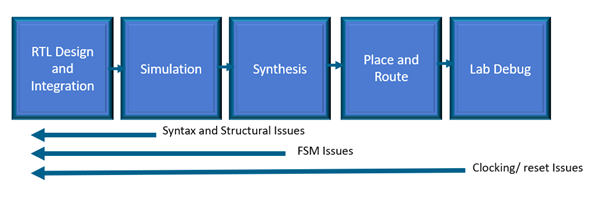
Find and fix issues as you code, not late in the design cycle
Blue Pearl’s Visual Verification Suite, used early and often in the design process as opposed to as an end of design/sign-off only tool, significantly contributes to design security, efficiency, and quality, while minimizing chances of field vulnerabilities and failures.
To learn more about the Visual Verification suite, please request a demonstration https://bluepearlsoftware.com/request-demo/
